The Defend-O-Tron was designed to be used in various defense scenarios.
Here are some example use cases of where you can deploy the Defend-O-Tron, however you can deploy in most scenarios that meet the requirements.
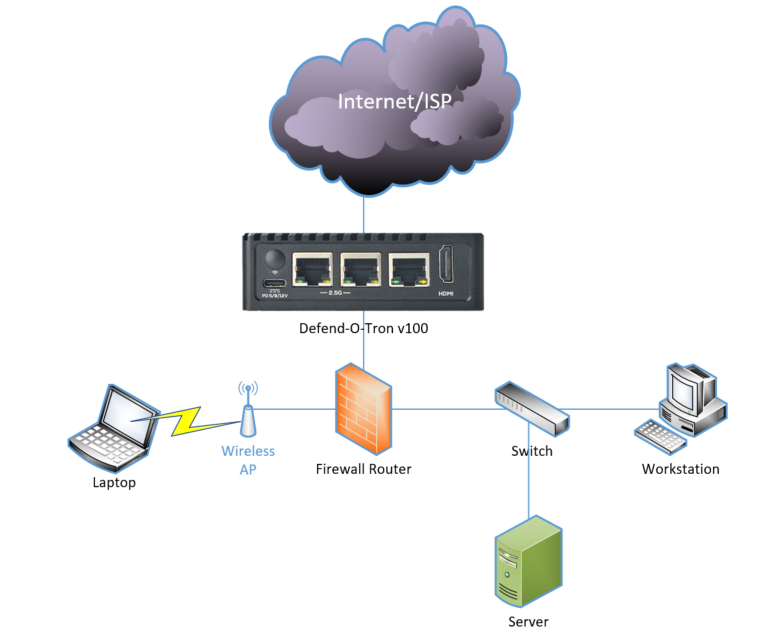
¶ Single Office/Location
This use case has the Defend-O-Tron deployed at the main office which is a single location. There's a server that serves HTTP/s to the internet and the Defend-O-Tron can be fed logs from the web server in order for it to defend against HTTP/s exploits.
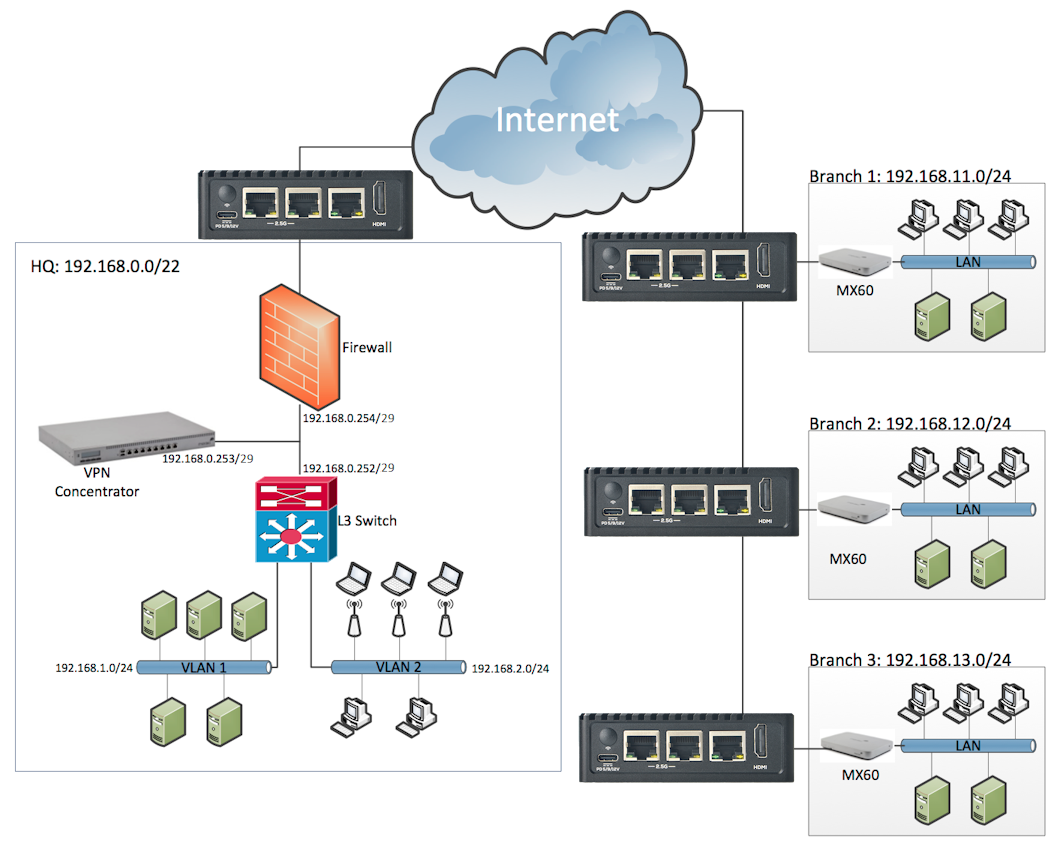
¶ Branch Office
This use case has the Defend-O-Tron deployed at the head office as well as each branch office. Here the branch offices have a Cisco Meraki deployed behind the Defend-O-Tron, allowing the Meraki system to be managed centrally. The Defend-O-Tron web interface will allow you to manage additional units, in this expample each unit uses the VPN capabilities of the Meraki network to route back to the central office.
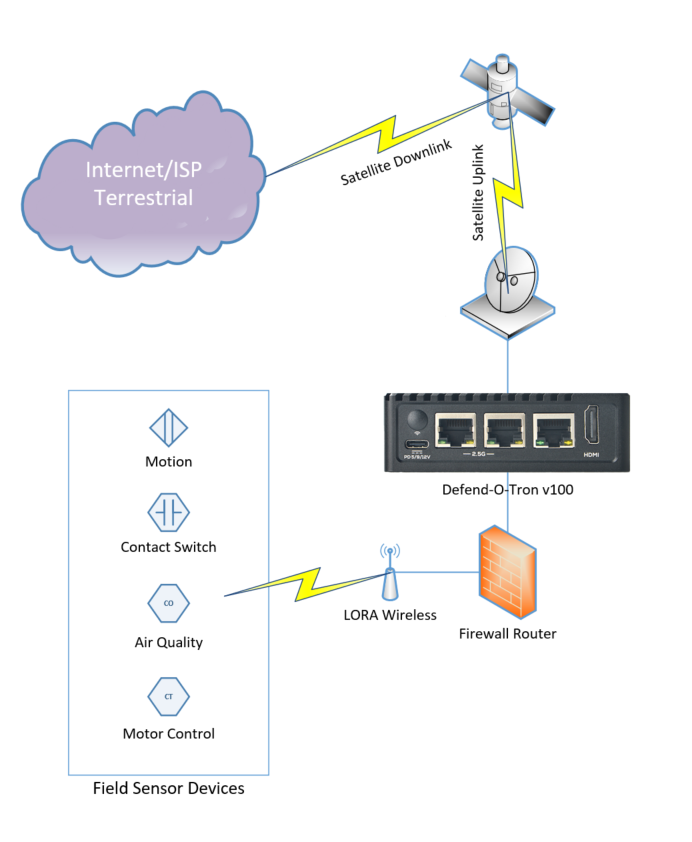
¶ IoT Remote Sensing
This use case has the Defend-O-Tron deployed at the central IoT uplink location. Because the device has low power requirements it's a good fit in locations with limited power resources. With the addition of the serial interface it can be managed via a console communication application such as Minicom
Recently MITRE introduced an embedded threat model aimed at IoT and other types of embedded devices, providing a good opportunity to implement IoT edge defenses in your environment. You can read more here MITRE EMB3D