¶ Transparent
Yes the Defend-O-Tron is configured to be transparent to the Internet and your firewall/router, allowing regular traffic to flow un-hindered through the device. Potential attackers will only see your firewall as a service endpoint.
¶ Threat Intelligence Sharing
The Security Engine runtime revolves around a few simple concepts:
It reads logs
Those logs are parsed via parsers and eventually enriched
Those normalized logs are matched against the scenarios that the user has deployed
When a scenario is "triggered", CrowdSec generates an alert and eventually one or more associated decisions:
The alert is here mostly for traceability and will stay even after the decision expires
The decision, on the other hand, is short-lived and tells what action should be taken against the offending IP/range/user...
This information (the signal, the associated decisions) is then sent to Local API and stored in the database
As you might have guessed by now, the Security Engine itself does the detection part and stores those decisions. Then, remediation components can "consume" those decisions (via the very same Local API and apply the remediation.
Crowd sourced aspect
Whenever the Local API receives an alert with associated decisions, it shares the alert's meta-information with our central API:
- The source IP address that triggered the alert
- The scenario that was triggered
- The timestamp of the attack
This is the only data that is sent to our API, and it is processed on our side to be able to redistribute the relevant blocklists to all the participants (that's your Defend-O-Tron!).
¶ Inline Protection
The Defend-O-Tron stands between the ISP and your router/firewall, if at anytime you feel there’s an issue with it you can simply remove it from the path. No extra software to install or special configurations to make.
¶ Log feeding
Pre-configured to accept syslog ingress to be parsed by the Crowdsec engine. Logs can be sent to the device from other systems that may have detected an unwanted connection attempt and the device will add that to the blocked list.
¶ Centralized IDS
Deep packet inspection is done via Suricata in realtime and the results are fed into Crowdsec for bouncing and alerts. All the rules for both Crowdsec and Suricata are updated daily to ensure your protected against emerging threats.
¶ Crowdsec API
The Crowdsec LAPI is accessible via the mamagement port. Connect external bouncers to the Defend-O-Tron for added defense, whether you bounce in NGINX, Traefik, Apache or pfSense Crowdsec has a bouncer for you.
¶ Cloud Dashboard
This is an optional setup, where you can view in more detail the defense metrics and additional information about each bad actor. The cloud dashboard also allows you to remove a banned IP address just in case it was detected erroneously.
¶ DNS Protection
Every wonder what sites and services your users are visiting? The built-in DNS and DNS defense filter will let you know. We're powered by Adguard a leading DNS defense software. The DNS filter, which is optional to use, can guard against unwanted ads and phishing sites. It also has the ability to block a whole range of sites based on service types (e.g. NetFlix, Ebay, TikTok, etc.)
¶ Simplified Management
The simple web interface is all you need to manage the Defend-O-Tron. There's even a terminal shell built-in so you don't have to SSH to the device (although you still can it you want to). Software updates and security lists are automatically maintained daily.
¶ Modern SOC
We've put the latest ARM64 bit Cortex-A55 processor behind the Defend-O-Tron. At 2ghz and 4 cores you have a robust device to tackle your defenses. There's even an NPU on-chip for future A.I. inference right on the device.
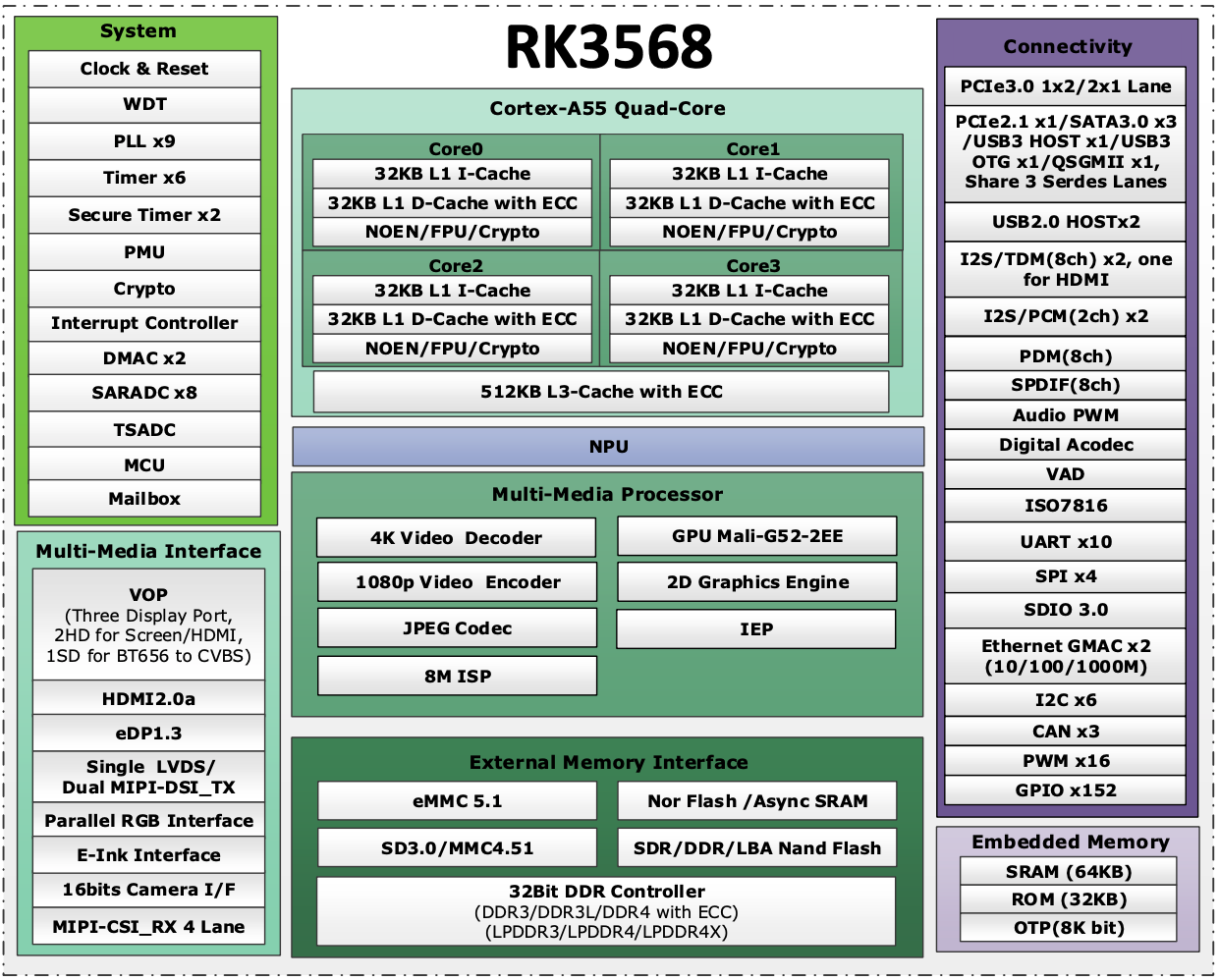
The Rockchip RK3568 SOC is a high-range general-purpose SoC, made in 22nm process technology, integrated 4-core ARM architecture A55 processor
¶ Open Hardware
The Defend-O-Tron was built with the intention of the open hardware and right-to-repair concept in mind. We don't have the closed vendor locked mindset of some of the big guys. You have access to electronic schematics and code that runs on the Defend-O-Tron, you can upgrade the logging disk as well.